With over 40% of the web powered by WordPress, addressing WordPress security issues is more critical than ever. As cyber-attacks multiply, even beginner users need to be aware of potential WordPress vulnerabilities.
Not only do these threats risk your website’s functionality, but they also put user data and overall trust in danger. Understanding and addressing these challenges is the first step in ensuring a safe and strong online presence.
13 Most Common WordPress Security Issues and Vulnerabilities
Walking through the basics of WordPress means understanding the source of various WordPress security issues. Often, vulnerabilities emerge from outdated software, poor configurations, or even overlooked settings. When exploited, these weak points can lead to unauthorized access, data breaches, or even total site takeover.
Understanding where WordPress vulnerabilities come from and their possible effects is crucial for every WordPress site user, no matter their tech skills.
1. Malware and Viruses
At its core, malware, short for malicious software, is designed to infiltrate, damage, or exploit any device, network, service, or program. A virus is a type of malware that attaches itself to clean files and spreads throughout computer systems. In the context of a WordPress site, common culprits include backdoors, unexpected downloads, and malicious redirects.
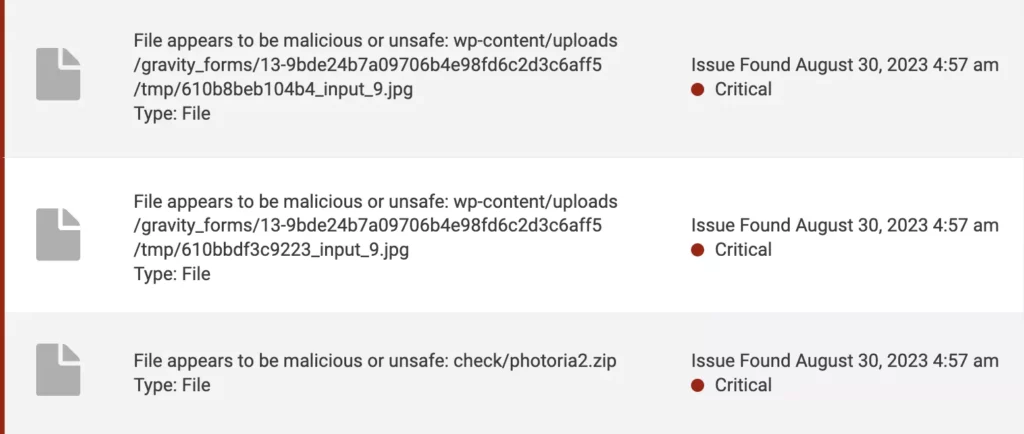
Specific to WordPress sites, users may encounter malware disguised as plugins or themes. Sometimes, even legitimate software can be compromised if not sourced from reputable theme or plugin developers or platforms.
The dangers of malware and viruses in WordPress websites are numerous. They can lead to a complete site takeover, rendering you powerless over your own content. Worse, they might steal sensitive user data, harming both your visitors and your reputation.
Best Practices and Solutions:
- Regularly do malware scanning of your website with a trusted WordPress security plugin.
- Only download plugins and themes from reputable sources, like the official WordPress repository.
- Stay updated on the latest malware trends and threats within the WordPress community.
2. Brute Force Attacks & The Perils of Weak Passwords
In today’s digital age, one of the most common threats WordPress users face is brute force attacks. This type of cyber threat involves hackers making relentless attempts to guess your login credentials. Think of a brute force attack like a thief tirelessly trying every key on a keychain until they find the one that opens the door. The whole idea of a brute force attack is based on persistence, with hackers counting on the fact that users often use easily guessable passwords.
Contrast this with the security risks of weak passwords. If a brute force attack is a burglar trying every key, then using a weak password is like leaving your main door slightly open. It invites trouble and makes the hacker’s job all too easy.
To combat brute force attacks, it’s really important to use strong, unique passwords. In this vast sea of digital threats, a strong password acts as your lifeboat. Relying on tools like password managers can be incredibly beneficial. They not only assist in generating a complex password but also securely store them, ensuring you’re not the low-hanging fruit for cybercriminals targeting your site.
Best Practices and Solutions:
- Craft secure passwords that mix together uppercase letters, lowercase letters, numbers, and symbols.
- Commit to periodic password changes, especially in crucial areas like your WordPress admin dashboard.
- Lean on reputable password managers to both generate and safeguard your complex passwords.
3. Outdated Core Software, Plugins, and Themes
Every piece of software has its vulnerabilities, including the core WordPress software, plugins, and themes. As these security vulnerabilities become known, WordPress developers release updates to patch them. Failing to update your WordPress website components leaves your site exposed. In essence, outdated software is like an open invitation for hackers, granting them easy access points to exploit.
The process of regular updates isn’t just about adding new features or improving performance. It’s a critical security measure. By consistently monitoring and updating, you’re ensuring that your website benefits from the latest WordPress security patches, keeping potential threats at bay.
Best Practices and Solutions:
- Ensure you are applying security updates to WordPress core, plugins, and themes. Before updating, check for compatibility to avoid potential issues.
- Regularly review and remove any plugins or themes that are no longer maintained by their developers.
- Use monitoring services or plugins that notify you of available updates or potential WordPress vulnerabilities.
4. Low-Quality Hosting
While it’s tempting to opt for budget-friendly hosting solutions, especially when starting out, this decision can come with significant drawbacks. Cheap or shared hosting often means you’re sharing resources with countless other sites. If any one of those sites is compromised, yours could be at risk too. Additionally, low-quality hosts might not prioritize security features or regular backups, leaving your website vulnerable to attacks or data loss.
On the other hand, managed WordPress hosting or Virtual Private Server (VPS) solutions offer a more tailored environment for WordPress sites. These options typically come with enhanced security protocols, faster performance, and dedicated resources. Investing in quality hosting is like investing in a solid foundation for a building—it’s essential for long-term stability and safety.
Best Practices and Solutions:
- Research hosting providers thoroughly, prioritizing their security features and track record.
- Consider upgrading to managed WordPress hosting or VPS for enhanced security and performance.
- Regularly backup your website, either through your hosting provider or using dedicated backup WordPress plugins.
5. Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting, commonly known as XSS, is a type of WordPress security vulnerability where attackers inject malicious scripts into web pages viewed by users. Unlike other attacks targeting the website itself, cross-site scripting targets the users of the website. When a user interacts with a compromised page, the malicious script runs, potentially accessing cookies, session tokens, or other sensitive information from the user’s browser.
The implications of a cross-site scripting attack are far-reaching. Attackers can steal user browser data, impersonate victims, or even redirect users to malicious websites. Given the stealthy nature of these attacks, they often go unnoticed until significant damage has been done.
Best Practices and Solutions:
- Use a WordPress security plugin or a Web Application Firewall (WAF) service that offers real-time monitoring and protection against XSS vulnerabilities.
- Regularly clean and check all inputs, outputs, and data that your website processes.
- Educate yourself and any site administrators about the risks of cross-site scripting (XSS) to ensure safe practices when managing content or adding new plugins/themes.
6. DDoS Attacks
DDoS, which stands for Distributed Denial of Service, is a type of attack where multiple compromised systems are used to flood a target, typically a web server, with an overwhelming amount of traffic. The primary aim? To exhaust the server’s resources, causing it to become inaccessible to legitimate users.
The ramifications of successful DDoS attacks can be severe. Beyond just an interrupted service, it can severely hurt website performance, and prolonged attacks can lead to significant downtimes. For businesses, this translates to lost revenue, damaged reputation, and frustrated users.
Best Practices and Solutions:
- Consider using Content Delivery Networks (CDNs) like Cloudflare, which offer built-in DDoS attacks protection.
- Regularly monitor your website’s traffic patterns to detect any unusual spikes, which might indicate the beginnings of a Distributed Denial of Service attack.
- Invest in specialized DDoS protection services or tools that can help absorb and disperse malicious traffic.
7. SQL Injections
SQL injections are a concerning facet of web security, where attackers exploit vulnerabilities in a website’s structure. They manage to manipulate a website’s PHP code, paving the way to inject malicious SQL commands into its database query. This manipulation shifts the dynamics, making the MySQL database execute these harmful instructions instead of its regular functions.
The consequences of SQL injections can be severe. Attackers, leveraging these methods, might exploit vulnerabilities, specifically targeting WordPress vulnerabilities, to gain unprecedented access. This unauthorized access allows them to view, edit, delete, or even add new data to the system. Imagining the breach scale, they could easily view sensitive user details, alter essential site content, or bring the whole website down, leading to alarming website malfunctions or privacy invasions.
Best Practices and Solutions:
- It’s always important to clean inputs. By doing this, you ensure that any data introduced into your website, whether through forms, URL parameters, or other means, is thoroughly cleaned of any harmful elements.
- One effective way to fix SQL injection risks is to use prepared statements along with specific input methods. This method ensures your SQL database isn’t directly susceptible to malicious user inputs.
- Consider installing a WordPress security plugin. Such tools are designed to vigilantly monitor and shield your site from SQL injection attempts and other threats.
8. Search Engine Optimization / SEO Spam
One subtle but damaging form of attack on WordPress sites is Search Engine Optimization spam. Here, hackers inject spammy content or malicious links into your website, often concealed so regular visitors don’t notice. These injections might promote unrelated products, link to malicious sites, or contain keyword-stuffed content.
The consequences aren’t just aesthetic. SEO spam can seriously harm a website’s reputation with search engines. As the search engine identifies these spammy elements, it may lower the site’s ranking. In extreme cases, it might remove the site from search results altogether, leading to decreased organic traffic.
Best Practices and Solutions:
- Install and regularly update reputable WordPress security plugins that scan for and remove SEO spam.
- Monitor search engine rankings and site statistics for sudden drops or unexpected keywords.
- Regularly review your site content, especially user-generated content, for any unfamiliar or suspicious links and text.
9. Phishing
Phishing is a deceptive tactic where attackers trick individuals into revealing sensitive information, like login credentials or personal data, by pretending to be a trustworthy entity. In the WordPress ecosystem, this could manifest as fake plugin update alerts or misleading admin login prompts.
When users fall for these tactics, they’re essentially handing over the keys to their website, enabling attackers to seize control, steal data, or commit various other malicious acts.
Best Practices and Solutions:
- Always double-check the URL when logging into your WordPress site. Phishing sites might look identical but will have a different or suspicious URL.
- Be careful of unsolicited communications urging immediate action, like unexpected password resets or plugin updates from unfamiliar sources.
- Use two-factor authentication for an added layer of security, making it harder for attackers even if they have your password.
10. Undefined User Roles
Every user on your WordPress site should have a defined role, be it an administrator, editor, or subscriber. Not setting clear user roles and permissions can be likened to having an open-door policy at a secure facility—anyone can walk in and access areas they shouldn’t.
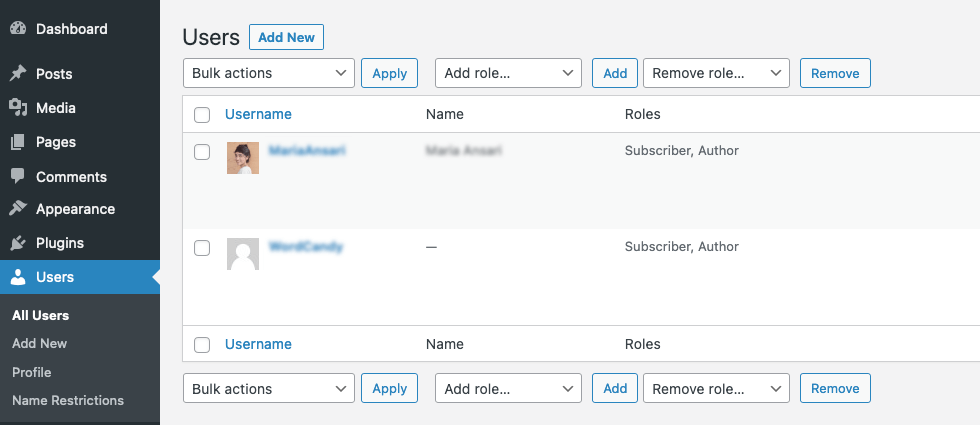
If user roles aren’t tightly defined, it opens avenues for misuse. A user with too many privileges might unknowingly make harmful changes. Worse, in the hands of someone with malicious intent, these undefined roles could lead to intentional harm or data breaches.
Best Practices and Solutions:
- Regularly audit user roles, ensuring each user has only the permissions they absolutely need.
- Limit the number of administrators on your site. Not everyone needs full access.
- Use WordPress plugins or tools that allow for more detailed control over user permissions, so you can customize roles to fit your site’s unique needs.
11. Untrusted Themes and Plugins
In the vast world of WordPress websites, there’s no shortage of plugins and themes. With some premium options coming with a hefty price tag, the allure of “nulled” (or pirated) versions of these tools can be tempting. However, these unauthorized versions often come with hidden malicious code that can have severe implications.
Nulled plugins or themes, seemingly beneficial due to their ‘free’ status, might actually be trojan horses. By installing them, users could unknowingly be adding backdoors, spyware, or SEO spam to their websites.
Spotting the Red Flags:
- The source site seems dubious or unfamiliar.
- The WordPress plugin/theme is offered for free, but it’s typically a premium product.
- User reviews or comments indicate unexpected behaviors or security issues after installation.
Deploying untrusted software can lead to a myriad of problems, from simple spam ads popping up on your website to severe WordPress security issues like data theft, changing the look of your site without permission, or even a complete site takeover.
Best Practices and Solutions:
- Always download plugins and themes from reputable sources, like the official WordPress repository or trusted developers.
- Keep a regular check on your website for unexpected changes or activities.
- Use WordPress security plugins that can scan and identify malicious code in themes or plugins.
12. Exposed wp-config.php file
The WordPress configuration file, wp-config.php, is one of the most critical files in your WordPress installation. It houses sensitive data like database connection details and unique security keys. In essence, it’s the guide to the backend of your site.
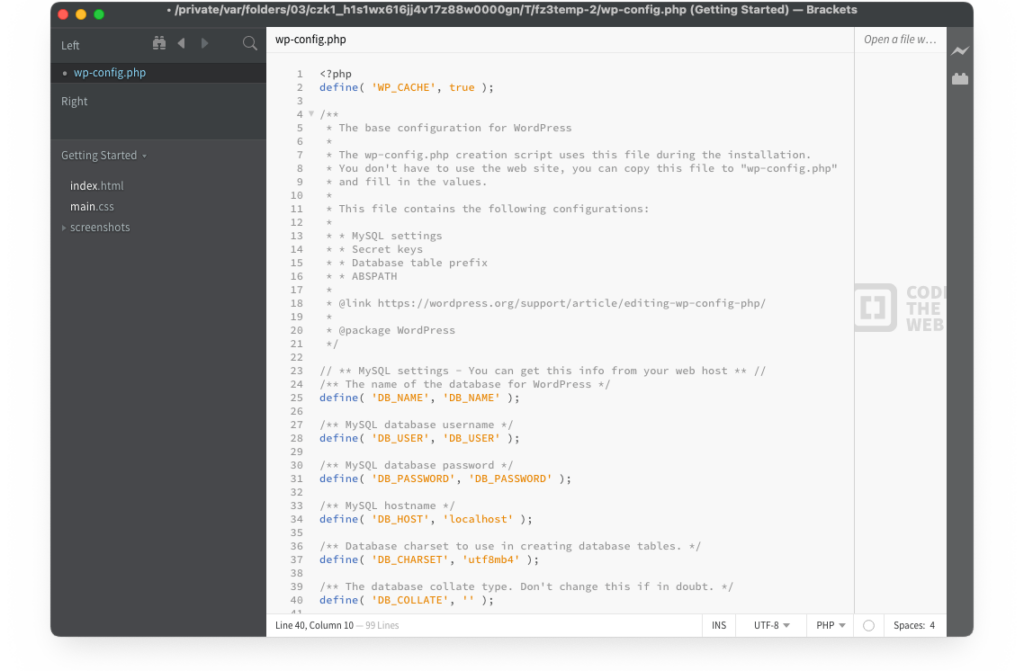
If attackers access this file, it’s like handing them a roadmap to your site’s most vulnerable points. They can manipulate content, inject malicious javascript code, or even delete the entire website.
Best Practices and Solutions:
- Set the correct file permissions to ensure only the required individuals or processes can read or modify ‘wp-config.php’.
- Move ‘wp-config.php’ above the web root, making it inaccessible via the web browser.
- Regularly back up the file and your entire website, so you can quickly recover in case of any mishaps.
13. Insecure Permissions
In a WordPress environment, every file and directory has a set of permissions. These permissions dictate who can read, modify, or execute them. While they might seem technical and tedious, understanding and setting them correctly is crucial for your WordPress security.
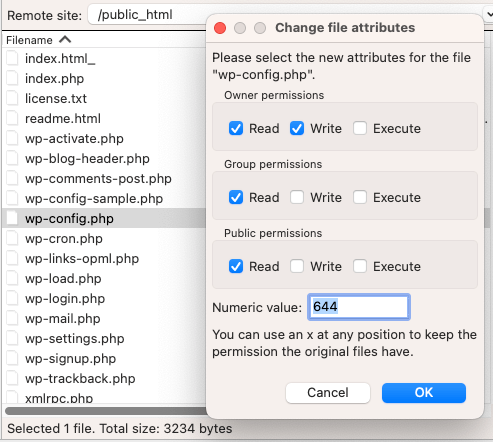
Overly generous permissions are like leaving your house’s doors wide open. It allows malicious actors easier access to inject code, remove files, or cause other havoc on your site.
Best Practices and Solutions:
- Regularly review and adjust file and directory permissions, ensuring they’re as restrictive as possible without hindering your site’s functionality.
- Avoid the infamous “777” permission setting, which gives everyone read, write, and execute permissions — this is a massive security risk.
- Use WordPress security plugins or hosting services that can assist in correctly configuring permissions and alert you of any insecure settings.
Conclusion
In the vast landscape of the digital world, threats are ever-evolving, and hackers are continuously finding potential security vulnerabilities to exploit. Addressing WordPress security issues should be a top priority for WordPress site owners. A universal approach to security just won’t cut it. It’s imperative for WordPress users to adopt a multi-layered defense strategy. Just as a castle wouldn’t rely solely on its outer walls to fend off invaders, your website should employ various protective measures at different levels.
But beyond tools and tactics, an essential component of website security is education and awareness. As the digital world advances, so do the methods and motives of those with malicious intent. It’s crucial to stay updated, be informed of the latest threats, and continuously adapt. Just like any skill or practice, cybersecurity requires ongoing learning and vigilance.
In essence, safeguarding your WordPress site is an ongoing journey, not a destination. Equip yourself with the right tools, knowledge, and a proactive mindset. Your website is a valuable asset; give it the protection it truly deserves.


